Threat Intelligence
Dangerous Invitations: Russian Threat Actor Spoofs European Security Events in Targeted Phishing AttacksDecember 4, 2025
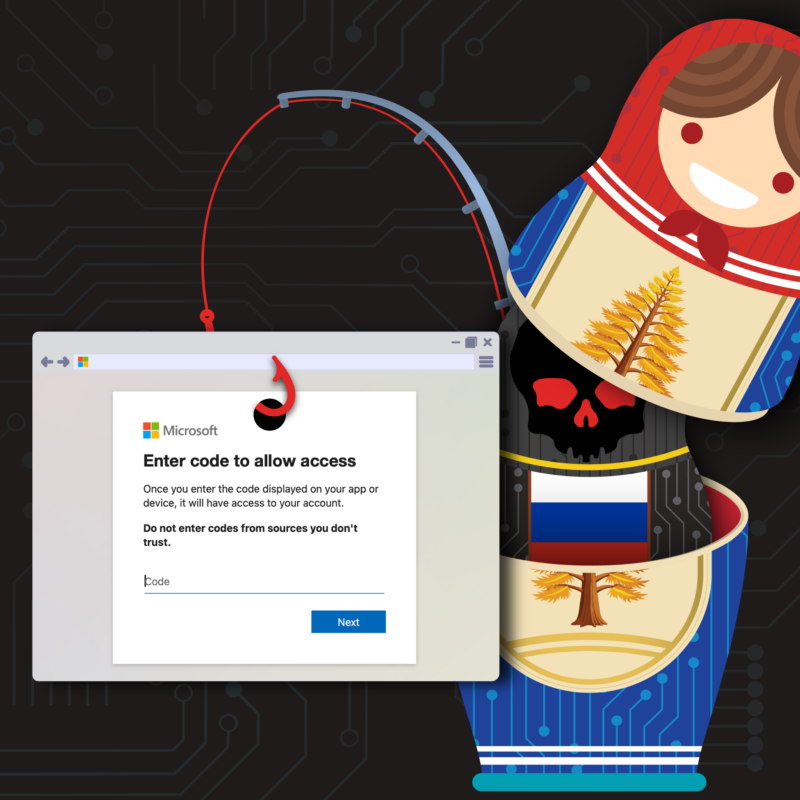
In early 2025, Volexity published two blog posts detailing a new trend among Russian threat actors targeting organizations through the abuse of Microsoft 365 OAuth and Device Code authentication workflows to […]
Read More